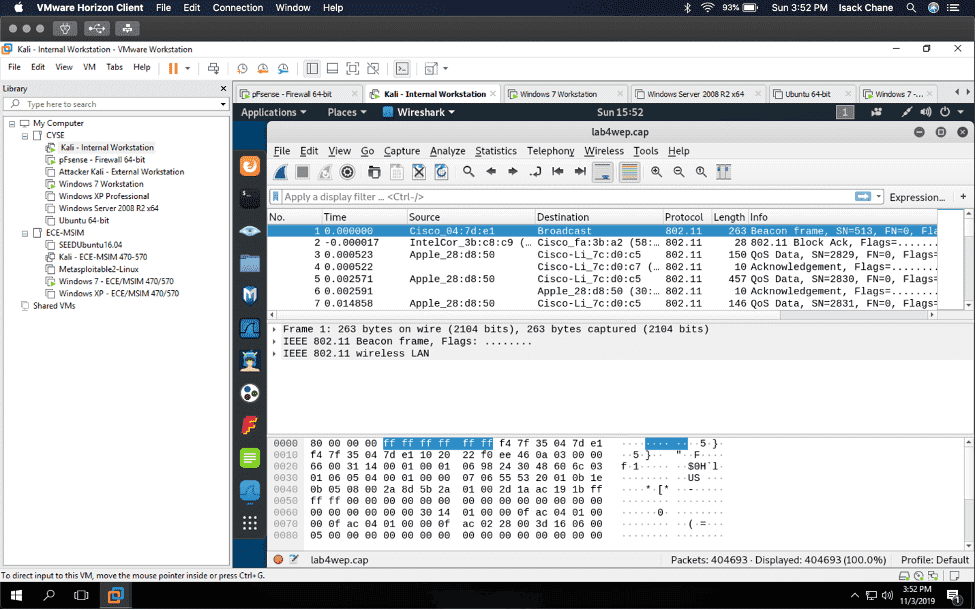
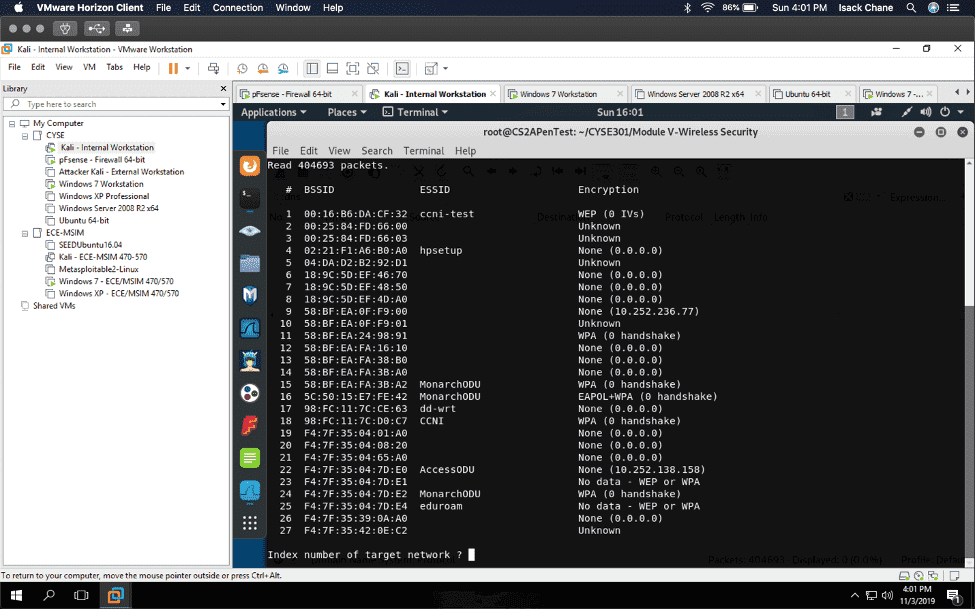
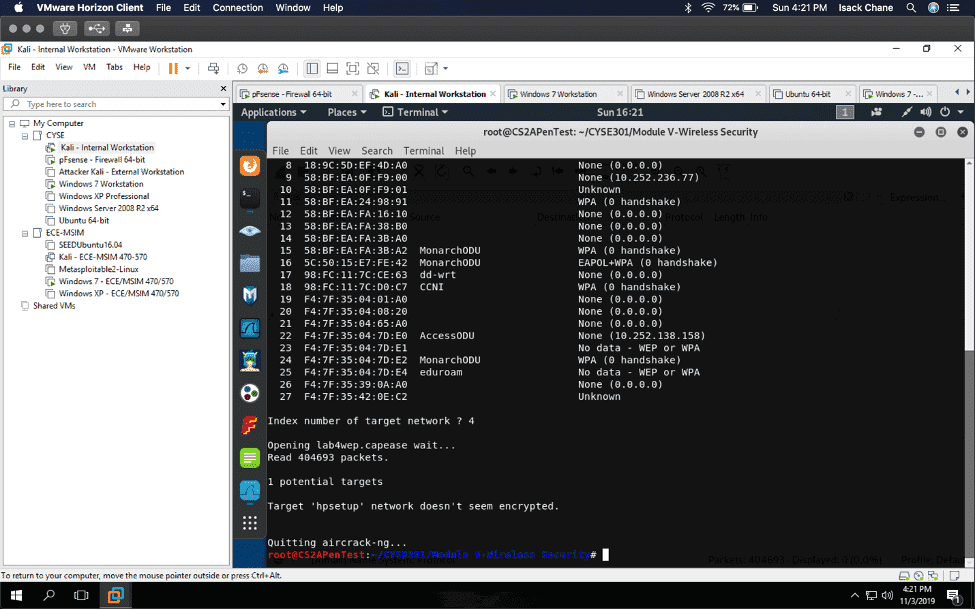
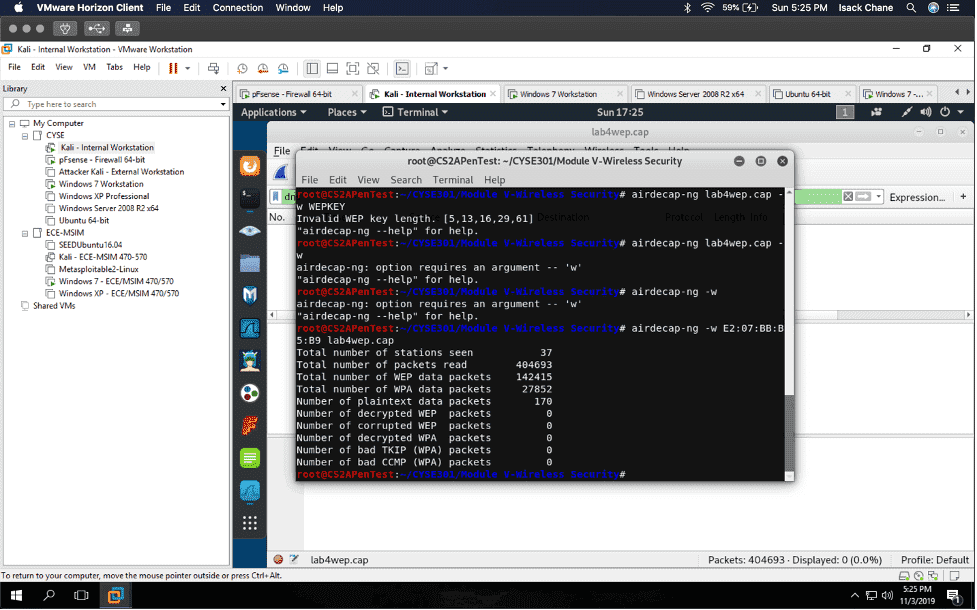
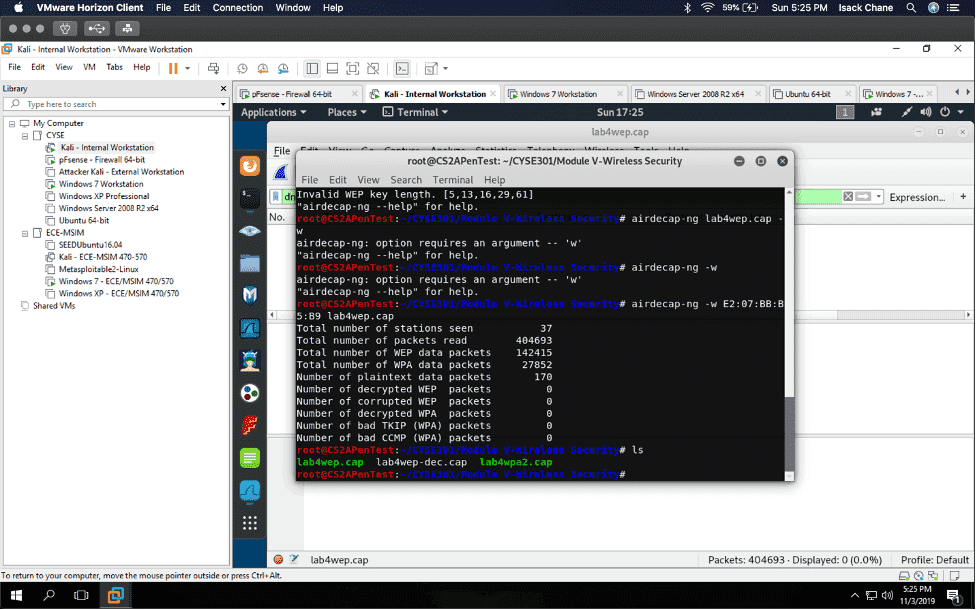
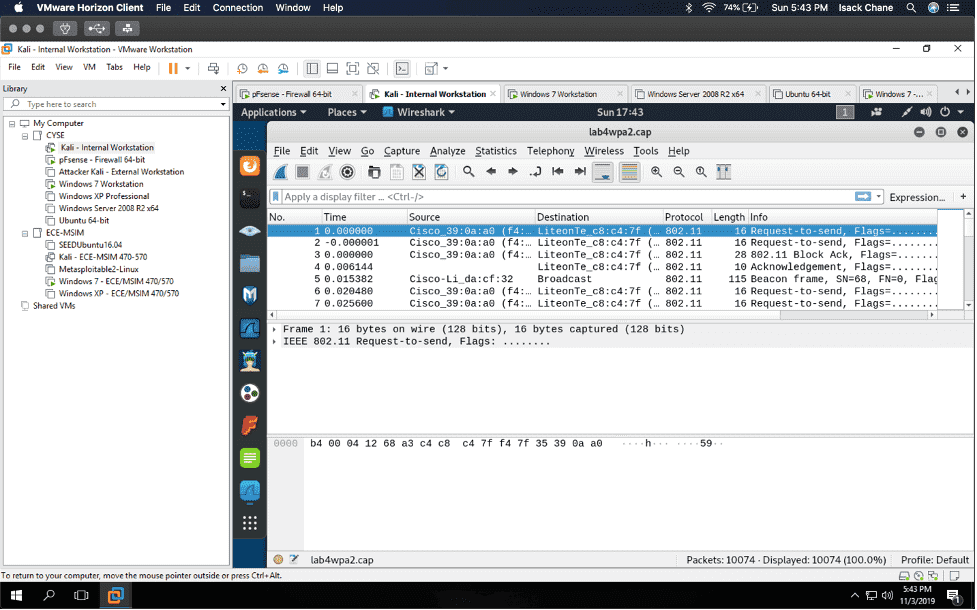
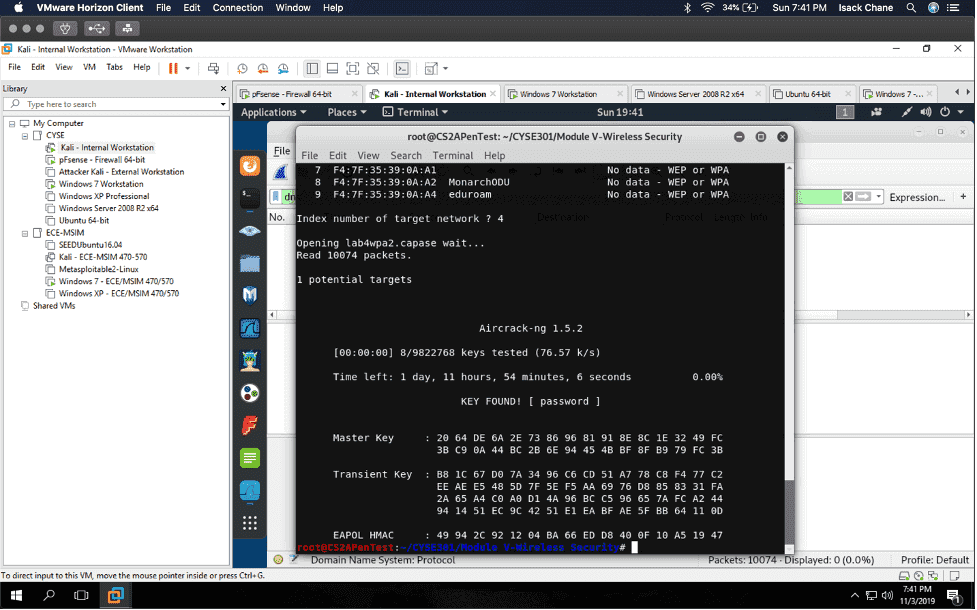
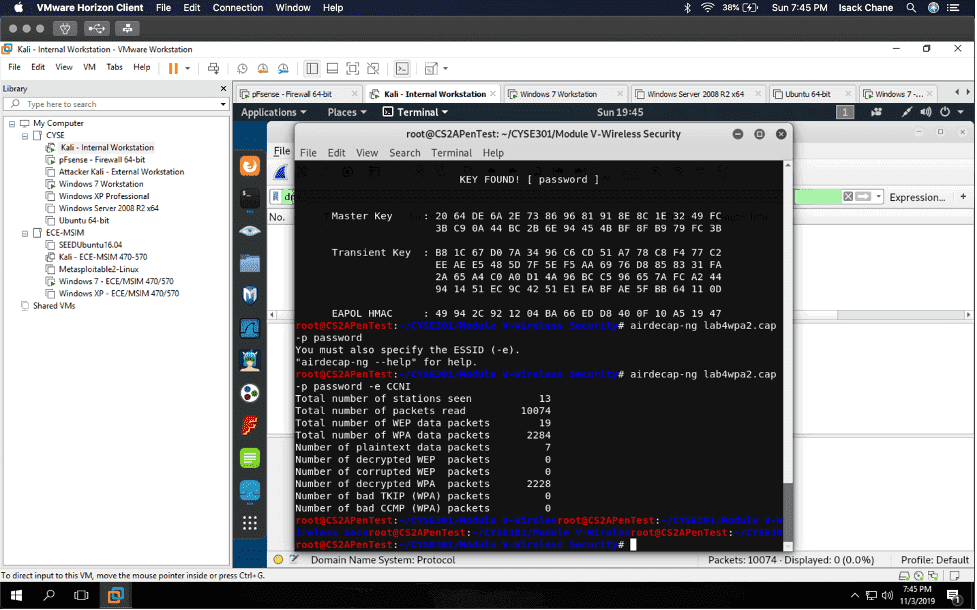
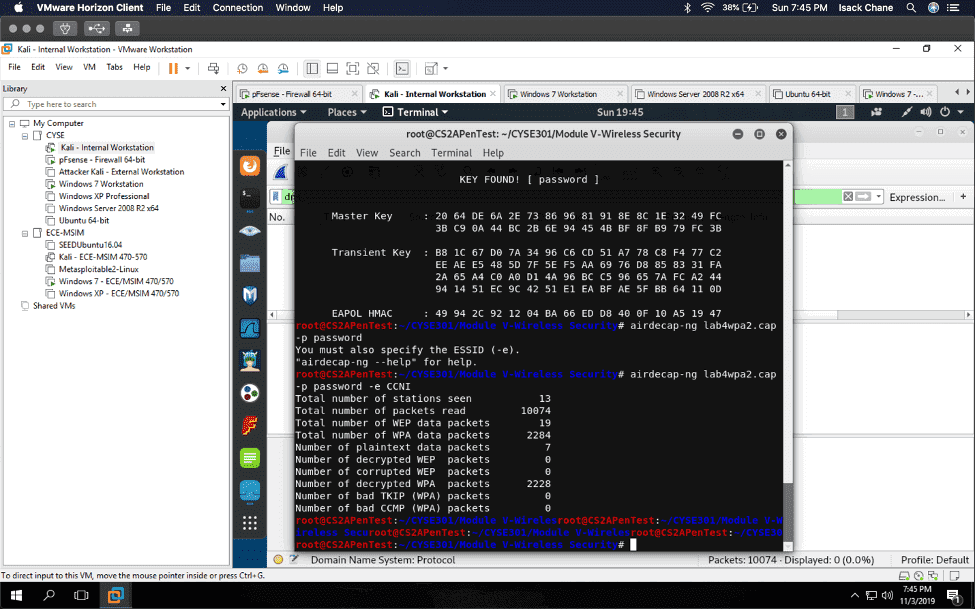
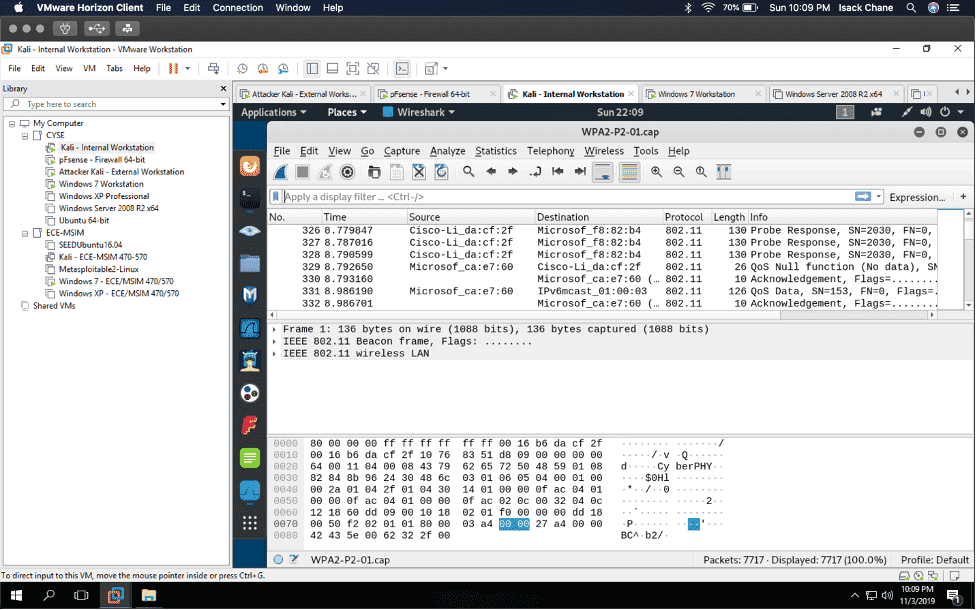
In my “Cybersecurity Techniques and Operations” class also known as “CYSE 301.” I did a project using the software Wireshark to analyze a traffic file. I had to first implement a dictionary attack and find the password used for encryption. Then I had to decrypt the encrypted traffic.
The details of the assignment included each student being assigned a new WPA2 traffic file for analysis. Also, each student would use a dropbox link that was assigned to use to share a download file to a Windows 10 host machine in our Cyberseucirty environment. Then, we would again implement a dictionary attack and find the password used for encryption and lastly, decrypt the encrypted traffic. Below are screenshots of me doing this assignment.
I found a lot of information in Wireshark, given that Wireshark is a packet sniffer application. I found packets on my network that were a majority TCP, UDP, and ICMP. Wireshark can also be used to analyze encrypted TLS traffic. I was visiting some websites like Cisco ODUOnline video archive and it showed on the Wireshark traffic. Before I cracked the password in the terminal I found an online hash WPA2 hasher for my Midas ID. I then found the corresponding file I needed to decrypt. I saved the file from one VM environment to another using the H drive. I then transferred it to Kali using the VM share and was able to find the password using the terminal in Kali.